2018GoogleCTF-Just-In-Time
Introduction
This is a small write up and recurrence for 2018GoogleCTF Just-In-Time.
Build environment
The version of chromium is 70.0.3538.9, we just need V8, so we can use OmahaProxy CSV Viewer to get the version of V8, the result is 7.0.276.3. And we can build it.
We should allow checkbounds optimization, just use
echo "v8_untrusted_code_mitigations = false" >> out.gn/x64.debug/args.gn
Analysis
The patch file addition-reducer.patch is as follow:
1 | diff --git a/BUILD.gn b/BUILD.gn |
It add a new reducer named DuplicateAdditionReducer, there are four kind of cases:
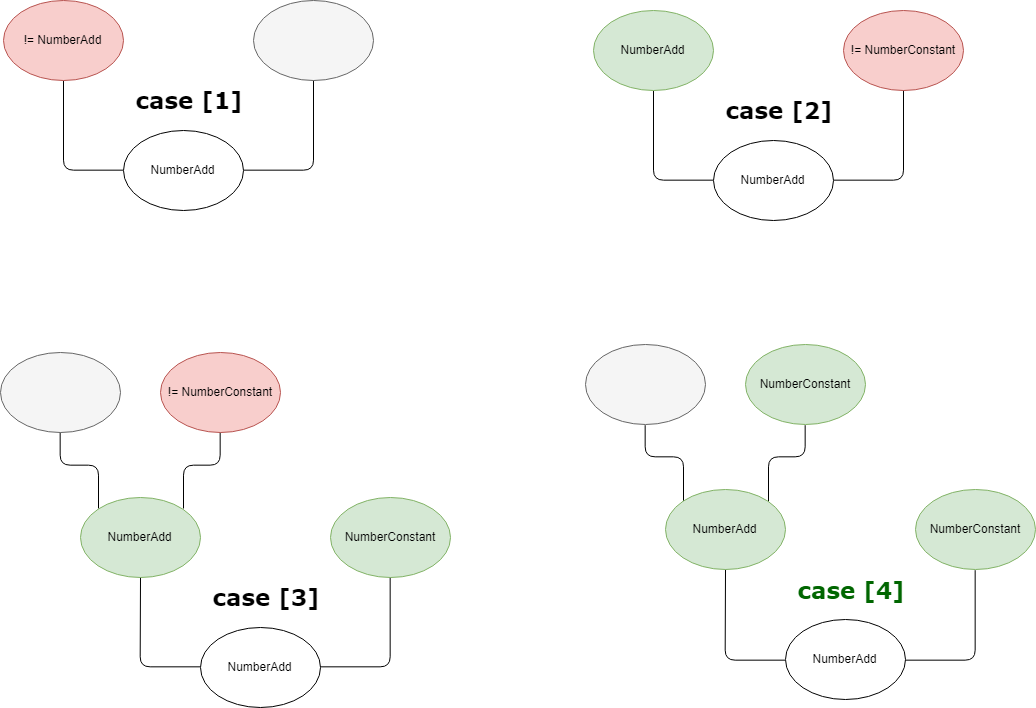
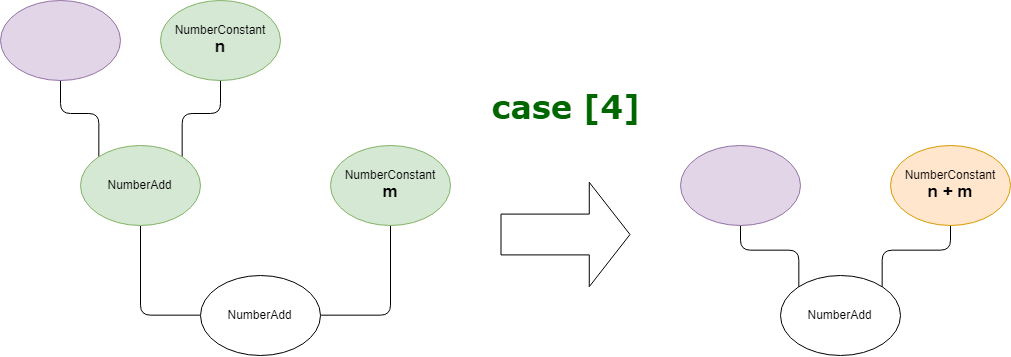
And it will optimized the expression x + 1 + 2 as x + 3:
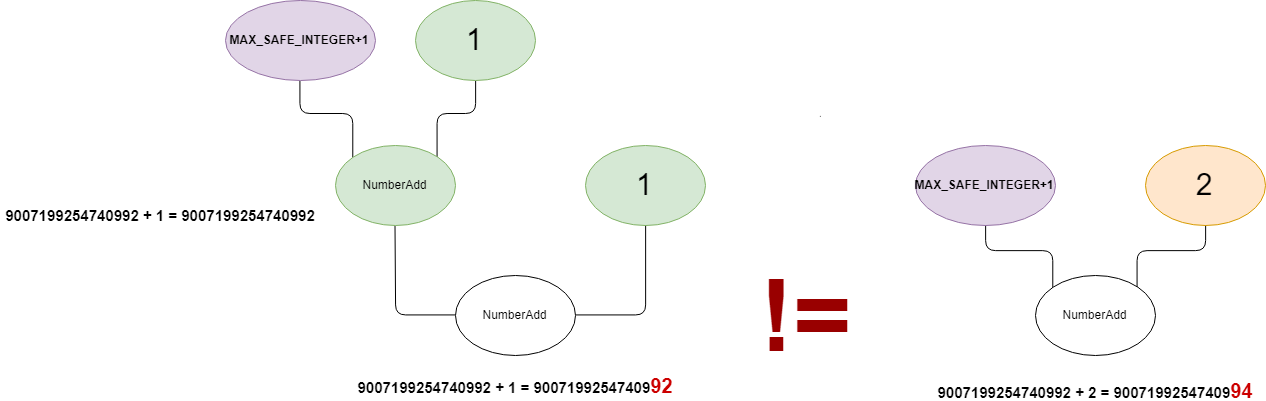
The NumberConstant use IEEE-754 doubles to save the number. There is a precision loss bug in it:
1 | d8> var x = Number.MAX_SAFE_INTEGER + 1 |
So x += 1; x +=1; may not be equivalent to x += 2:
1 | d8> var x = Number.MAX_SAFE_INTEGER + 1 |
Therefore, those two graphs are not equivalent.
Just test the poc:
1 | var arr = [] |
We can see there is a CheckBounds in typer phase:

And it be optimized in the simplified lowering phase:

If we look at the output, we can find there is a Out-of-bounds read result:
1 | $ ./d8 --allow-natives-syntax test.js |
So we have an OOB, we can use this to get shell.
Exp
1 | var buf = new ArrayBuffer(16); |
Reference
https://github.com/google/google-ctf/tree/master/2018/finals/pwn-just-in-time
